
In the wake of the MGM ransomware attack, it's clear that enhancing cybersecurity is a top priority for the gaming industry. However, this is not the only industry taking note. Any organization can be a potential target for cyberattacks, and breaches within a company network can result in systems outages, operational disruption, and critical data being stolen.
Reports on the MGM breach state that a social engineering attack initiated through a phone call set the cyberattack in motion. The MGM case isn’t the first, it won’t be the last. It is important to learn from the incident as it is crucial for organizations to have security best practices in place. Every employee should be properly trained and made aware of the various methods that bad actors may use to try to infiltrate networks. Many employees do not keep an eye out for individuals who are impersonating coworkers through spoofed email addresses or phone numbers. Authentication protocols, such as multi-factor authentication (MFA), can help avoid these issues through verification of an individual's identity so that imposters do not gain access to networks for malicious purposes.
Social engineering is just one of many ways that bad actors can gain access to a network, with new methods and attacks being developed every day. To help protect against them, organizations need to fortify their security by educating employees with the right information and having a robust network structure in place that is composed of multi-layered security measures. Firewalls, antivirus software, advanced cloud security, event management and mitigation protocols, and strict cybersecurity compliance requirements are all established aspects needed to strengthen operational security.
Because of the recent threats to the resorts and casinos, let’s take a look at the basic security structure that may be currently implemented.
Data Storage:
• On-Premises Data Centers: For storing sensitive customer data, transaction records, and other critical information.
• Storage Area Networks (SAN): High-performance SANs are used to store and manage vast amounts of data efficiently.
Internal Network:
• Servers: House various applications, including gaming software and customer databases.
• Firewalls: Multiple firewalls to protect the network from external threats.
• Switches and Routers: Manage internal traffic and ensure connectivity.
• Intrusion Detection and Prevention Systems (IDPS): Monitors network traffic for suspicious activity.
• Workstations and Electronic Gaming Machines (EGM): Used by staff and guests in day-to-day operations.
Here are some ways to build upon existing security structures to enhance their posture:
Data Storage:
• Cloud Storage: Migrate sensitive data to highly secure cloud platforms with advanced security features to reduce the risks of on-site data centers.
• Data Encryption: Implement end-to-end encryption for data in transit and at rest.
• Regular Backups: Maintain robust backup procedures and test data restoration regularly.
Internal Network:
• Zero Trust Architecture: Trust is never assumed, and each device, user, and application is rigorously authenticated and verified.
• Micro-Segmentation: Expand existing network into multiple isolated segments, ensuring that access to sensitive data is strictly controlled.
• Security Information and Event Management (SIEM): Implement advanced SIEM solutions to continuously monitor and respond to security events.
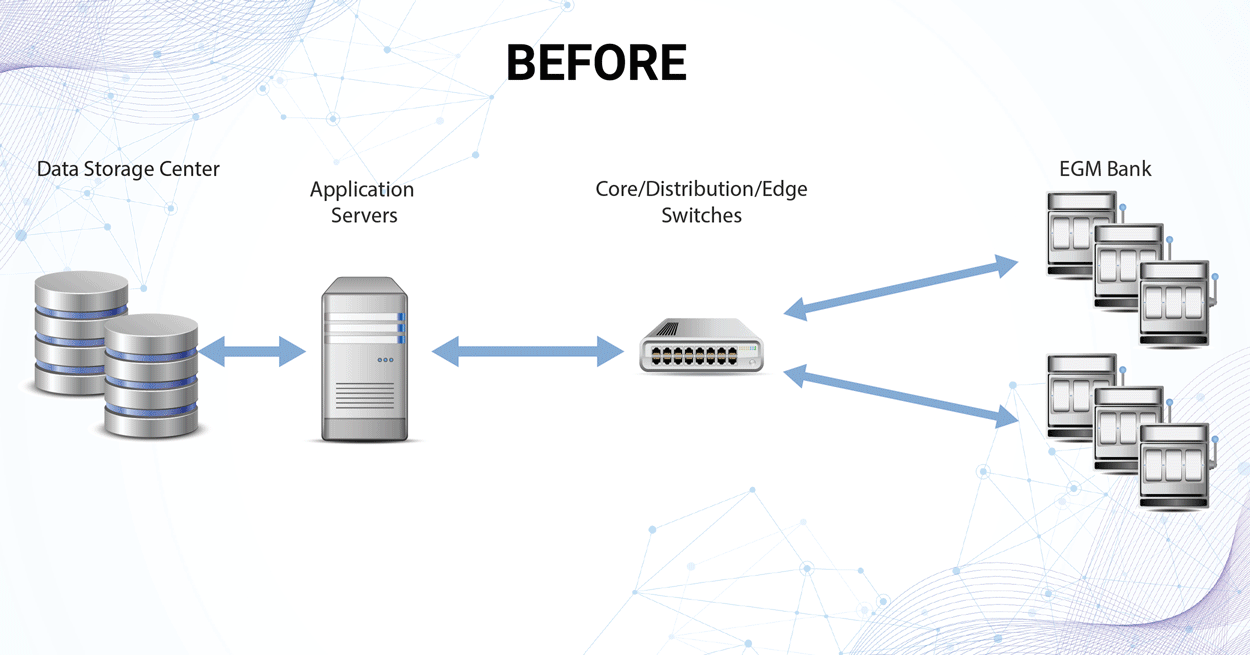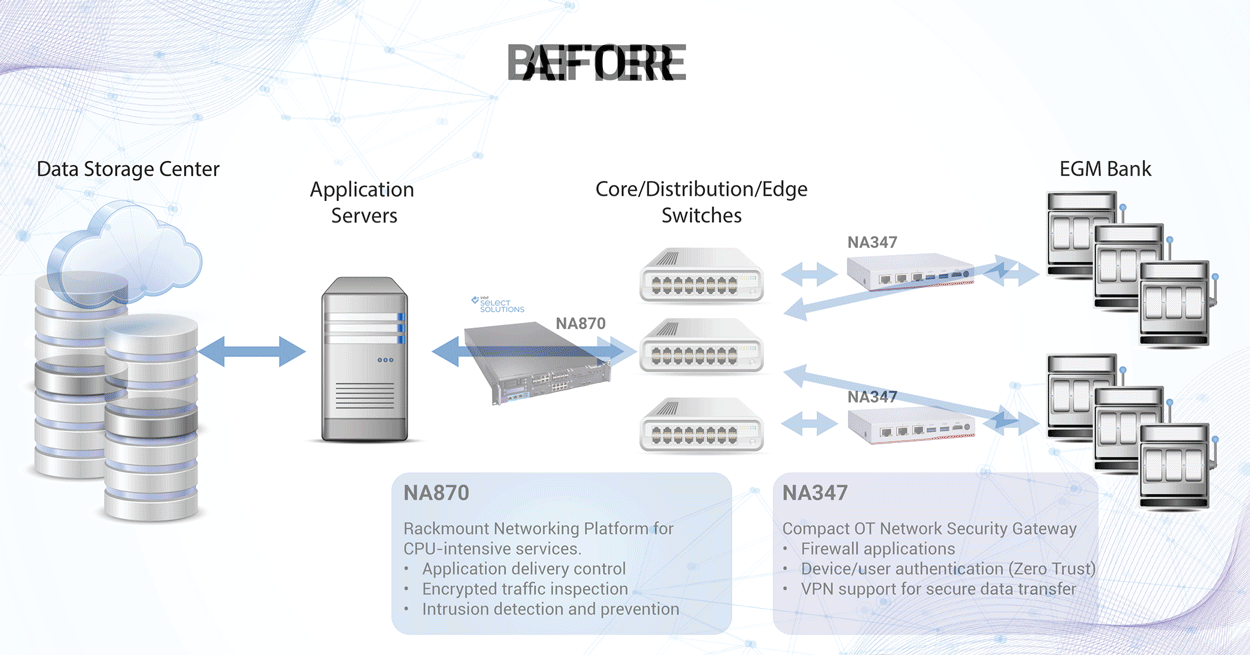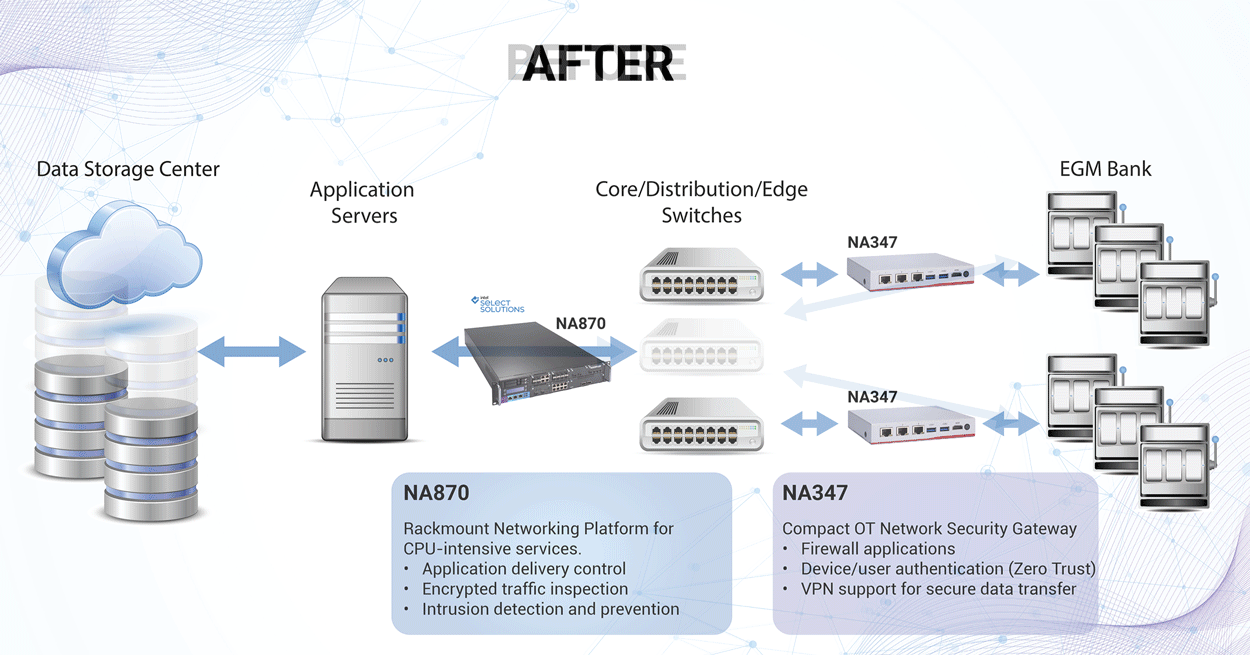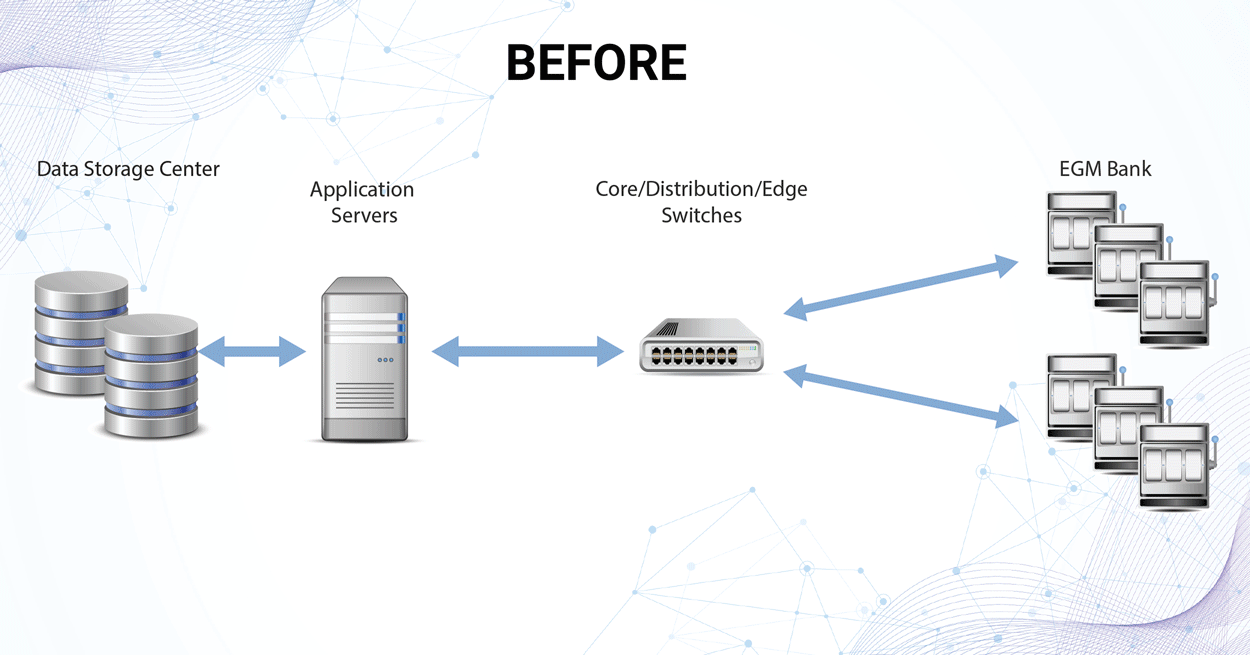
A layered security strategy is optimal for enhancing network security, making sure that a breach at one layer will not result in the entire network being immediately compromised. A multi-layered strategy that implements hardware firewalls and zero trust micro-segmentation will help prevent intrusions from moving laterally across a network. Hardware firewalls implemented through network appliances have the benefit of consistently protecting all devices connected to a network appliance. Compared to software firewalls which may share resources when installed on a different device, the network appliances used for hardware firewalls dedicate 100% of their resources to security purposes and minimize the potential for exploit.
Axiomtek can help reinforce your operations with cutting-edge networking products designed to safeguard your operations.
Discover the Axiomtek Advantage:
• Robust Hardware Firewalls: Our advanced networking solutions bolster your defense against cyber threats, ensuring your data remains impenetrable.
• Seamless Integration: Axiomtek products seamlessly integrate into your existing infrastructure, minimizing disruption.
• Real-time Monitoring: Stay one step ahead with real-time monitoring and threat detection capabilities.
• Compliance Assurance: Ensure compliance with industry regulations and protect your customers' sensitive information.
Don't wait for the next attack. Strengthen your operational security with Axiomtek and bet on a safer future. Reach out to learn more about our cybersecurity solutions. Your success is our priority!


